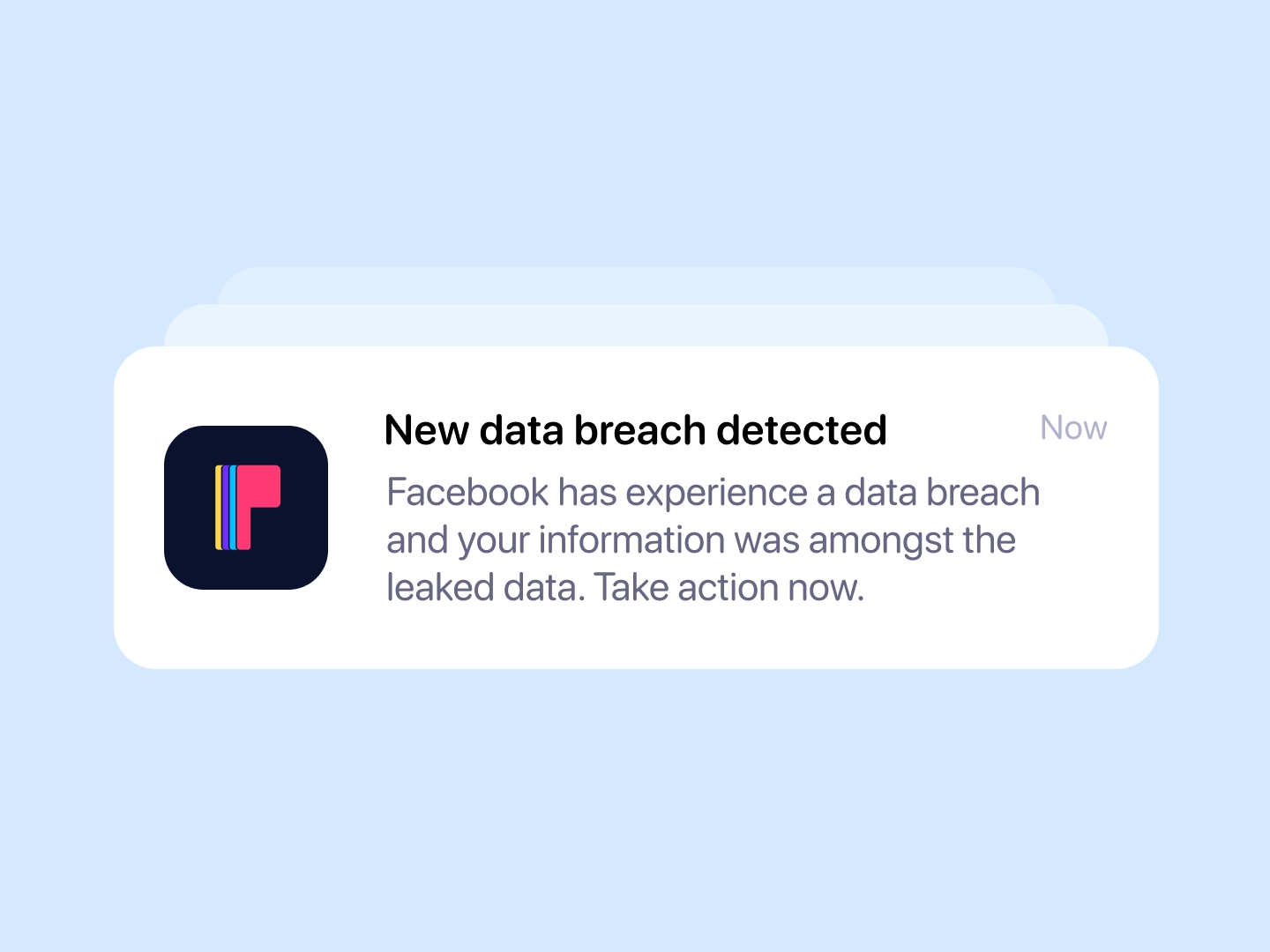
Monitor data that has been exposed in one or more data breaches.
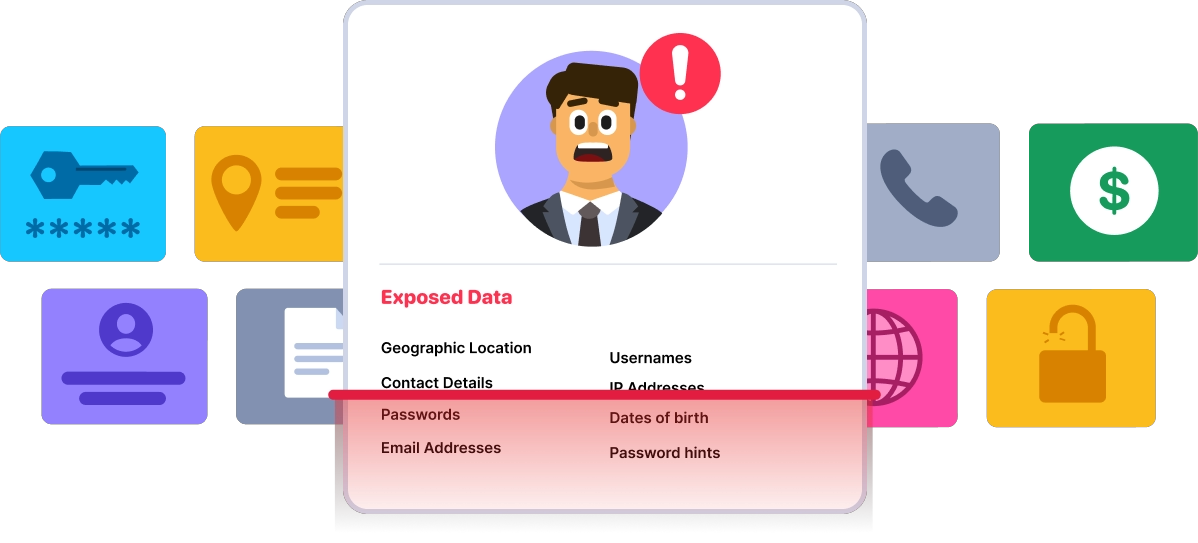
By constantly monitoring the dark web's underground marketplaces, forums, and illicit websites, we can swiftly detect any signs of unauthorized access to your information.
Our Dark Web monitoring tool continuously scans the dark web to identify compromised email addresses and associated leaked data.
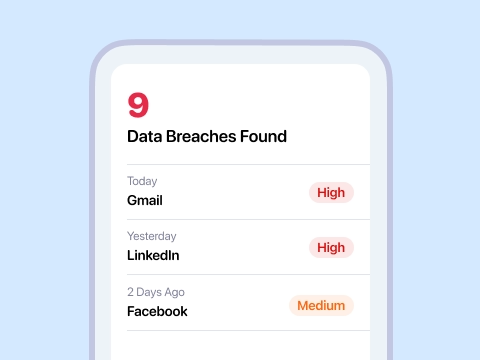
Receive detailed reports outlining which data breaches your email address has been linked to and what information was compromised.
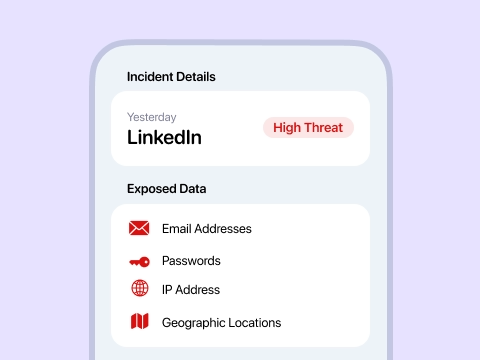
Get expert advice on the best steps to take next to mitigate the risk of further data leaks and protect your accounts from potential damages.
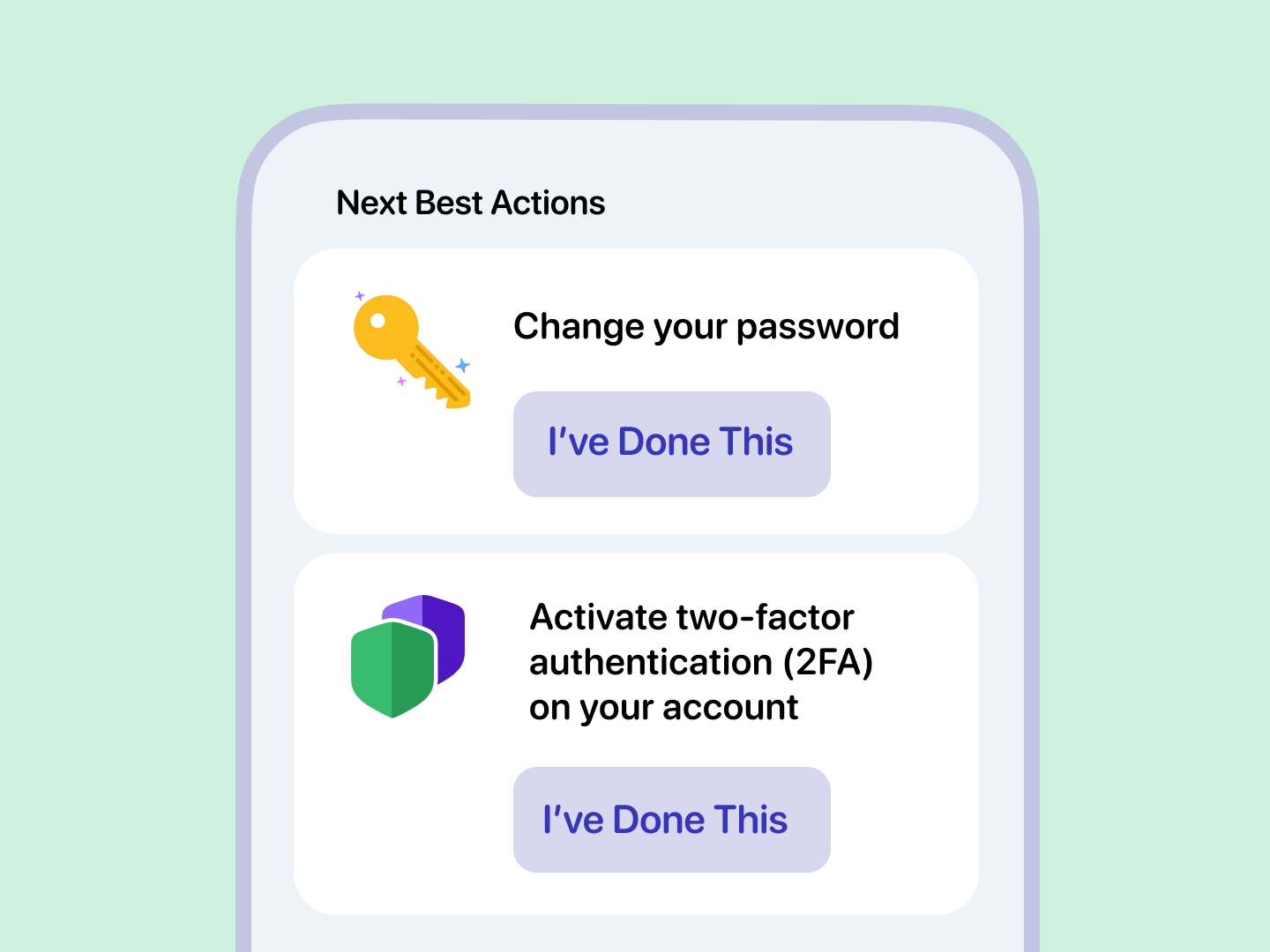
Rest assured knowing that our monitoring tool works round the clock to keep your digital identity safe and secure.
In a digital age rife with cyber threats, the need for vigilant defenses against data breaches is paramount. Dark web monitoring solutions offer a pivotal line of defense, utilizing sophisticated algorithms to swiftly detect compromised credentials and bolster cybersecurity measures effectively

90% of passwords can be cracked within seconds using automated tools

61% of people admit to using the same password across both personal and work-related accounts, potentially exposing sensitive corporate data.

The average time to detect and contain a data breach is 287 days, during which cybercriminals can exploit compromised credentials to inflict significant damage.

On average, individuals manage 191 passwords, but 25% of users admit to using just one or two passwords across all accounts.

Around 30% of users admit to sharing their passwords with others, increasing the risk of unauthorized access and data breaches.

Password-related breaches have increased by 450% over the past decade, indicating a growing trend of cybercriminals targeting weak authentication methods.

Don’t wait for an attack. Prepare your business with Prventi’s phishing simulation and innovative cybersecurity training.
No credit card required